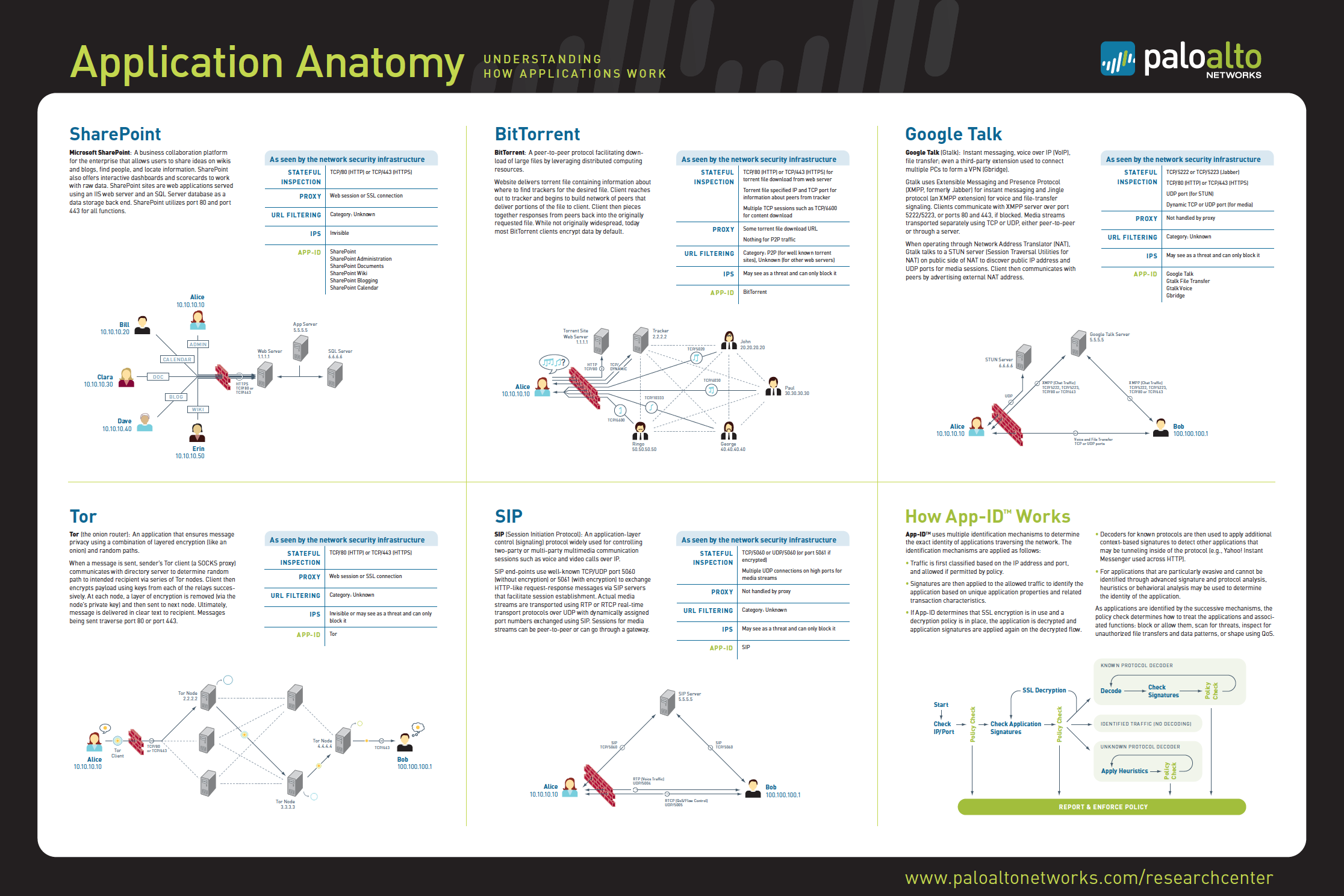
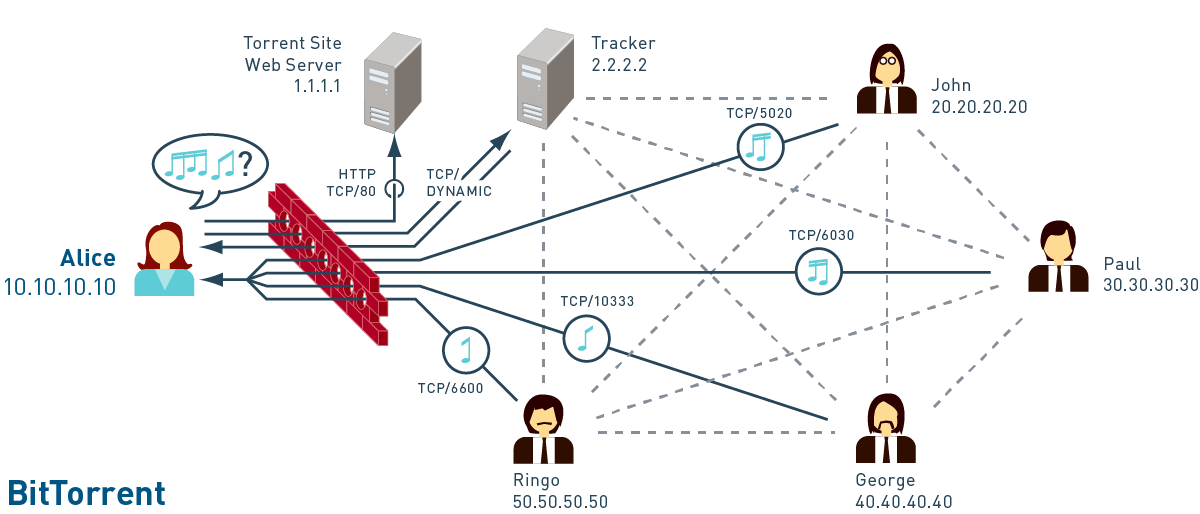
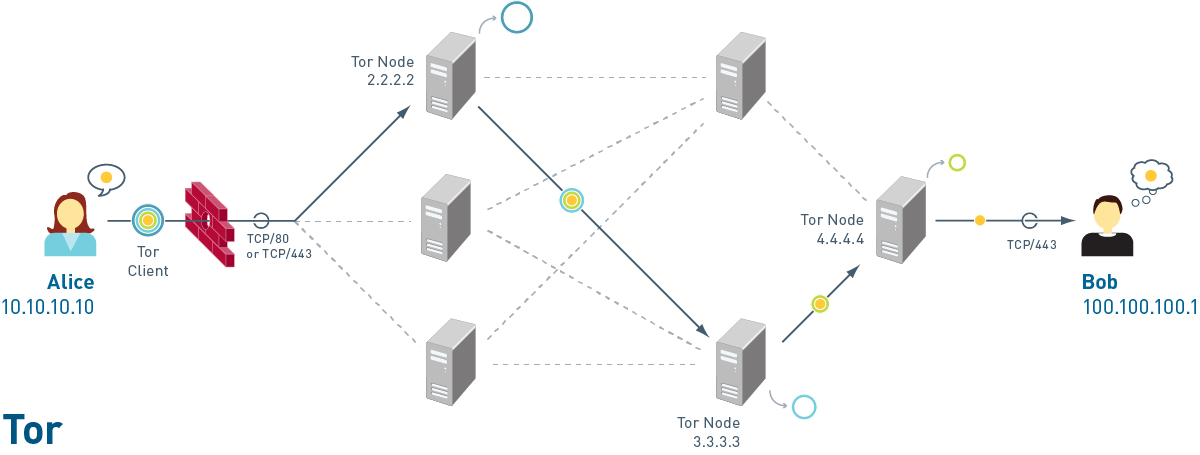
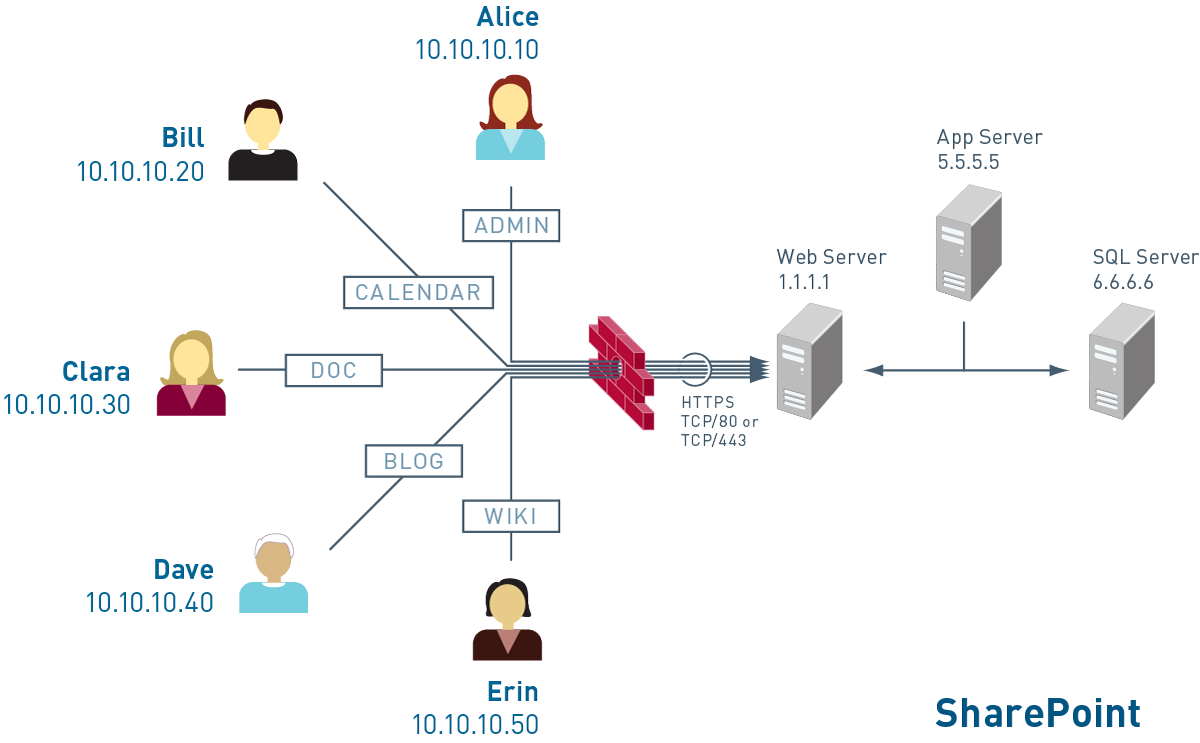
Understanding how different applications traverse the network is critical to knowing how to manage traffic and prevent vulnerabilities. We developed a series of diagrams for Palo Alto Networks that were made into a poster to educate their customers. A nod to the Fab Four on the BitTorrent diagram.